Robust Network Information Assurance with Next-Generation Cryptographic Technology
MESH NETWORK SECURITY
Reliable and secure communications are the backbone of what Rajant delivers through its Kinetic Mesh® technology. That is why we employ an expert Information Assurance (IA) team of embedded security engineers as well as ASIC, FPGA, and system engineers.

Next-Generation Cryptographic Technology
Rajant In-line Security Module (RiSM)
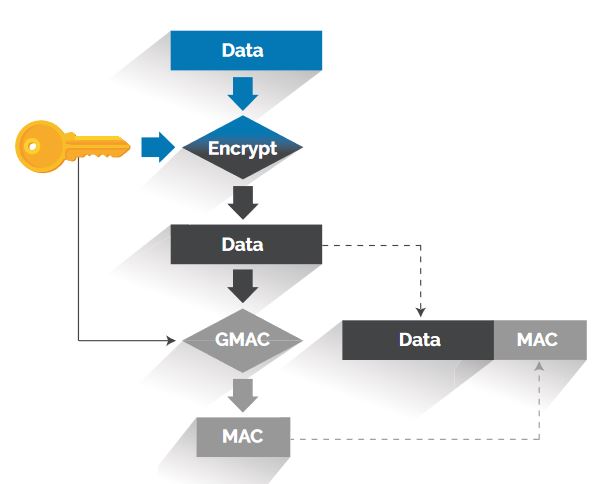
The team’s latest innovation is the Rajant In-line Security Module (RiSM). The RiSM provides military and government security for commercial needs. Any data deemed critical to your business can and will be protected at a FIPS level. The RiSM is a commercially available Hardware Security Module (HSM) that allows users to meet the latest NIST standards for encryption (FIPS 140-3) and requirements for protecting Sensitive but Unclassified (SBU) and Controlled Unclassified Information (CUI) data.
Together, they have developed next-generation cryptographic solutions to support the security requirements of an array of mission-critical applications, including those used for DoD’s most sensitive secure communications systems.
Rajant Wolverine
Scalable Architecture with Custom Programmability
The Rajant Wolverine is a fully programmable multi-chip design that leverages commercially sourced System on a Chip (SoC) FPGA and Application-Specific Integrated Circuit (ASIC) network processor. The Wolverine cryptographic module design is built for programmable flexibility to add new algorithms in the future while also meeting stringent U.S. government certification requirements. Wolverine contains advanced encryption and authentication algorithms using a fail-safe design to provide design flexibility for multiple Internet of Things (IoT) applications.
Wolverine utilizes industry-standard cells and IOs so that it can be easily migrated to meet higher performance requirements and/or to an ASIC design with minimal changes. Programmability also allows for customization of key management protocols such as EKMS and Tactical Key Management (TKM). Wolverine’s cryptographic algorithms support robust key rollover and future Over-The-Air-Keying (OTAK) solutions, which are essential methods for protecting classified data.
Secure Boot Capability that Goes Beyond Standard Security Processors
Wolverine’s Secure Boot capability governs what trusted software is allowed to run within the system and serializes the IP software/firmware modules upon initial load. This serialization means that every Wolverine-based solution has a uniquely encrypted software/FPGA image stored in flash while it is fielded. Therefore, if an adversary obtains a decryption key from one Wolverine unit, it will be useless on all other Wolverine units.
Wolverine can also serve as the root certificate and symmetric key storage element for the system. Certifiable anti-tamper capabilities ensure the most critical aspect of the security architecture, the keys, are inaccessible to an adversary.
Future-Proof While Meeting Stringent Certification Requirements
Wolverine can be easily modified to meet a wide range of future crypto processing needs for algorithm agility, I/O flexibility, and Key Management evolution. New algorithms can be added while continuing to meet stringent U.S. Government certification requirements, and footprint-compatible FPGA options are available to increase FPGA fabric size.
Order Today

Built for the Edge
Proven Everywhere
From mines and ports to energy fields and defense operations, Rajant delivers resilient, mobile, and intelligent edge networks that keep your mission moving.
Ready to talk specifics for your operation?
Get our products:
What We Offer
What’s Enabled
Kinetic Mesh® networks work autonomously to provide optimal connectivity across an organization’s dynamic environment of fixed and mobile assets, delivering robust applications in real-time.
This combination of technical functionality infuses Kinetic Mesh® networks with the adaptability, flexibility, intelligence, and mobility to help organizations across industries improve operational effectiveness, enhance quality of service, drive productivity, and generate increased ROI.

Total Mobility
Every node in a Kinetic Mesh network can act independently and with full routing capabilities, making it a true peer-to-peer network that is completely mobile-enabled.

Extreme Ruggedness and Security
Born from military and mining applications, our high-secure and encrypted outdoor mesh network is proven to withstand the harshest conditions.

Maximum Bandwidth Utilization
Kinetic Mesh networks make use of all installed radios to dynamically route wireless and wired connections over the best available links.

Rapid Scalability
While traditional mesh networks degrade as nodes are added, Kinetic Mesh networks grow stronger with each additional node. Nodes also self-configure for easy spin-out.

Proven Resiliency
With no single point of failure and self-healing capabilities, Kinetic Mesh networks guarantee uptime of your mission-critical applications. Offering a 100% Proven resiliency.

Assisting the entire team with the validation of the installation, configuration, and ramp-up of the testing phase was a highly rewarding experience. Through this project, I gained valuable insights into rail operations, which became a key learning opportunity for me. Additionally, I contributed to the delivery of training during the implementation phase, as part of the Sales Engineering team’s responsibilities.
Daniel Souza
Sales Engineer, LATAM – Rajant
You can’t drive video through a hill. There’s just not enough bandwidth. By putting up a Rajant network, it allows us to attach cameras to each of those Rajant nodes. The more we have, the more bandwidth we get.
Andy Stein
Think Vertical Now
The Rajant network is so reliable that you’re going to see an ROI almost immediately. We were able to see a $1M ROI in a year. We paid for the network within six months.
Brian Hunt
JR Simplot Company
The Kinetic Mesh is quite unique. The flexibility of the Rajant hardware is what’s critical.
Dale Birt
FTP Solutions
Open architecture enables interoperability between systems. Rajant is always looking ahead.
Ale Walker
Gray Solutions
For the Royal Wedding, it became quite apparent during the design process that using conventional point-to-point/multipoint would not suffice in the urban environment of Windsor, making Rajant’s mesh network a superior solution.
Thames Valley Police Member | Great Britain
Other wireless technologies, including the latest 5G, all have the same physical limitation: Wireless cannot pass through large, metal container stacks. Rajant’s Kinetic Mesh M2M technology allows the vehicles to talk to each other, which is critical to communicating fleet directions between container stacks.
Matthias Krause
DGWorld
Downtime is really the critical factor in our business. We just cannot afford interruptions, and with Rajant’s technology, we have virtually none.
Ed Darcy
President, Mealey’s Furniture
Our engineering team’s proposal to address this problem only worked because we used Rajant and its unique mesh feature, which is designed for this challenging environment.
Francisco Casals
CTO of Mining Tag Chile
You’ve got to be able to maintain connectivity and access your key performance indicators. Whether it’s sensors, people, or tablets, Rajant enables us to provide not only bandwidth and low latency but also support the needed applications.
Dustin Jurman
Rapid Systems
Using Rajant mesh technology, Kinross has reduced the need for technical staff to deploy repeaters in the network, while improving security and decreasing the number of personnel inside the mine.
Cleiton Arruda
Business Consultant, SITECH/Grupo Sotreq
We found Rajant’s solid track record in military operations reassuring. Its mesh networks have delivered many benefits in those rugged, dynamic environments.
Bob Wingle
Senior Technology Engineer | ASARCO Ray Mine
Webinar
Rajant Now – Making the Complicated Simple
Learn More
Frequently Asked Questions
What is Rajant Kinetic Mesh® technology?
Rajant Kinetic Mesh® is an Intelligent Edge networking technology designed for dynamic, mobile environments where traditional fixed infrastructure falls short.
Unlike conventional wireless systems, it enables continuous, adaptive connectivity across moving assets, people, and devices. Powering Industrial AI applications that demand resilience, low latency, and real-time decision-making.
How do Rajant’s BreadCrumb® wireless nodes enhance network connectivity?
Rajant’s BreadCrumb® nodes are the building blocks of a self-forming, self-healing Kinetic Mesh® network.
Each node communicates directly with every other, creating a web of redundant, high-throughput connections that ensure uninterrupted communication, even when conditions change or assets move.
This decentralized design eliminates single points of failure, maximizing uptime and mobility.
InstaMesh® vs. conventional point-to-point connections.
Conventional point-to-point networks depend on fixed links that can break under motion or interference.
Rajant’s InstaMesh® routing protocol dynamically reroutes traffic in real time, automatically choosing the fastest, most reliable path.
The result: continuous, mobile, and intelligent connectivity for operations that never stop moving.
What are the benefits of Rajant’s InstaMesh® for IIoT applications?
For Industrial IoT environments, InstaMesh® provides the low-latency, adaptive communication required to keep machines, sensors, and AI systems synchronized.
It delivers instant data exchange, self-healing reliability, and scalable capacity, empowering predictive maintenance, automation, and autonomous decision-making at the edge.
How can Rajant Kinetic Mesh support real-time tele-operations in mines?
Mining operations depend on remote visibility and control where connectivity is often limited.
Rajant’s Kinetic Mesh® delivers real-time communication and video streaming for tele-remote equipment and autonomous vehicles, even underground.
Its multi-radio BreadCrumb® nodes maintain reliable signal and low latency. Keeping operators safely in control from any distance.
Rajant Kinetic Mesh network vs. traditional WiFi solutions.
Traditional WiFi networks are static, fragile, and reliant on centralized infrastructure.
Rajant’s Kinetic Mesh® replaces those limits with a dynamic, peer-to-peer architecture, where every node acts as both transmitter and receiver.
This ensures continuous, adaptive coverage, ideal for moving assets and mission-critical applications where downtime is not an option.
Discover Rajant’s solutions for tunnel communications.
Tunnels and underground environments are notoriously difficult for wireless communication.
Rajant’s BreadCrumb® nodes create a linear, mobile mesh network that maintains signal integrity through long corridors, curves, and obstructions.
This allows real-time monitoring, voice, and video for mining, utilities, and public safety teams.
How does Rajant’s technology enhance machine-to-machine communication?
Rajant’s InstaMesh® routing enables machines to communicate directly and continuously, without depending on static access points.
This machine-to-machine (M2M) intelligence ensures critical data is shared instantly, fueling automation, robotics coordination, and AI-driven optimization across industrial environments.
Cost of implementing a Rajant Kinetic Mesh network.
Implementation costs vary based on network size, environment, and application.
However, Rajant’s decentralized design significantly reduces the need for fixed infrastructure, cabling, or complex configuration.
Resulting in a lower total cost of ownership and faster ROI compared to traditional networking systems.
How do BreadCrumb® nodes work in enhancing network resilience?
Each BreadCrumb® acts as a multi-radio, multi-frequency transceiver that maintains multiple simultaneous connections.
If one path is interrupted, InstaMesh® instantly reroutes data through another, creating always-on resilience that keeps communications live even under extreme conditions.
Maximize network uptime with Rajant’s solutions.
Rajant eliminates the single points of failure found in traditional networks.
Its multi-path, self-healing mesh keeps assets connected, even as they move, ensuring maximum uptime and operational continuity in industries where every second counts.
What industries benefit most from Rajant’s Kinetic Mesh technology?
Rajant’s Intelligent Edge networks power operations across mining, ports, logistics, defense, manufacturing, public safety, agriculture, and energy.
Wherever mobile assets, automation, and Industrial AI intersect, Rajant delivers real-time, reliable communication to keep data flowing and decisions immediate.
Comparing Rajant Kinetic Mesh with LTE solutions.
LTE depends on centralized infrastructure and licensed spectrum, creating latency and coverage limits.
Rajant’s Kinetic Mesh® offers a private, infrastructure-free alternative with ultra-low latency, flexible frequency use, and no dependency on towers or carriers. It’s built for mobility, autonomy, and data sovereignty.
Rajant Kinetic Mesh network integration with existing infrastructure.
Rajant networks are designed for seamless integration.
BreadCrumb® nodes connect easily with existing Ethernet, LTE, and satellite systems extending coverage, strengthening resilience, and modernizing legacy networks without disruption.
Do you sell direct?
Rajant primarily sells through our authorized partners and distributors, who bring deep expertise in deploying Intelligent Edge networking solutions across a range of industries.
This collaborative approach ensures customers receive tailored integration, local support, and end-to-end service from network design to deployment.
To find a Rajant distributor near you, visit our distributor page.